London, UK – November 2016 – Acunetix, the pioneer in automated web application security software, has announced the release of version 11. New integrated vulnerability management features extend the enterprise’s ability to comprehensively manage, prioritise and control vulnerability threats – ordered by business criticality. Version 11 includes a new web-based UI for greater ease-of-use and manageability, providing access by multiple users.
For the first time in the marketplace Acunetix is launching an
enterprise-level product that integrates sophisticated automated testing
technology with vulnerability management, at a price point accessible
to every development team. Chris Martin, CEO, Acunetix explains:
“Acunetix has for the past 12 years been at the forefront in web application security with its cutting-edge vulnerability scanning technology. With version 11 we have combined proactive scanning for web application vulnerabilities with the prioritization of mitigation activities. This integration helps security teams gain the intelligence they need to work more efficiently, prioritizing actions, assigning jobs and therefore reducing costs.”
The new web-based interface significantly improves the manageability
of the Acunetix on-premises solution, making it easy for less seasoned
security personnel to check the vulnerabilities within the company’s web
assets. In addition, user privileges can be automatically assigned.
Nicholas Sciberras, CTO, Acunetix, comments: “Version 11 helps organizations engaged heavily in application development by utilising a role-based multi-user system.”
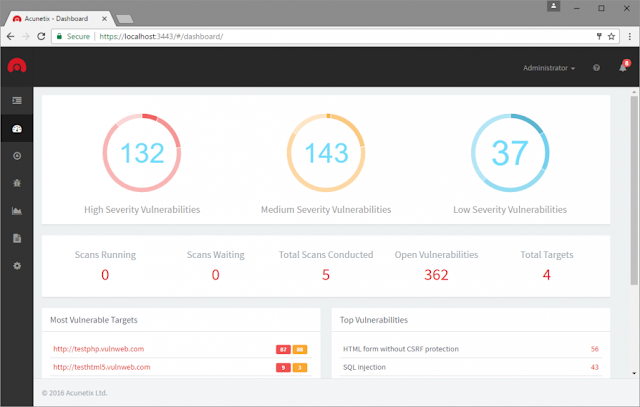
Inbuilt Vulnerability Management
New integrated vulnerability management features allow for the review
of aggregated vulnerability data across all Targets, prioritizing
security risks and therefore providing a clear view of the business’
security posture, while facilitating compliance.
New inbuilt vulnerability management features include:
- All Targets (web applications to scan) are now stored in Acunetix with their individual settings and can be easily re-scanned.
- Targets are displayed in one interface and classified by business criticality, allowing you to easily focus on the most important assets.
- Vulnerabilities can also be prioritized by the Target’s business criticality.
- Consolidated reports are stored in the central interface.
- Users can choose between “Target reports”, “Scan reports” or “All Vulnerabilities” report.
Web-based user interface
The user interface has been re-engineered from the ground up for
greater usability and manageability. The minimalist design focuses on
the most widely used and important features, doing away with extras
which cluttered the screen. Since the interface is now web-based,
multiple users can access it from their browser irrespective of the OS
used.
Role-based multi-user system
Acunetix version 11 allows the creation of multiple user accounts,
which can be assigned a particular group of targets. Depending on the
privileges assigned to the user, the user can create, scan, and report
on the targets assigned to him.This is particularly important for large
enterprises, which require multiple users to help secure their assets.
Standard, Pro and Enterprise Editions
Acunetix version 11 will be available in three main editions: Standard, Pro and Enterprise.
Standard Edition – is the entry level, ideal for
small organisations and single workstation users. The Standard Edition
offers the same level of vulnerability detection provided in the Pro and
Enterprise Editions and includes Developer, Executive Summary and OWASP
Top 10 reports.
Pro Edition – The Pro Edition allows outsourced or
insourced security professionals to group and classify asset targets. It
integrates with Software Development Life Cycle (SDLC) project
management or bug tracking systems, includes comprehensive compliance
reports, and integrates with top Web Application Firewalls (WAFs).
Enterprise Edition – includes full multi-user team
support and has the ability to deploy multiple scan engines managed by
the central system. The Enterprise Edition will be able to scale from 3
to unlimited users and up to 50 Acunetix scan engines.
 0Day to Buy
0Day to Buy