Best Hacking EBooks 2016 – In the Era of Teenagers many of want to Become a “Hacker” But In-fact It is not an Easy Task because Hacker’s have Multiple Programming Skills and Sharp Mind that Find Vulnerability in the Sites, Software and Other types of Application. If You want to become a Hacker you need to Spend most of the Time on your Computer to Learn New Technologies and Reading Hacking Book that can Help you to Become a Ethical Hacker. First You need to Read Hacking Books Carefully then Perform Practically not for Hacking Purpose Just only for Educational Purpose.
-

Penetration Testing Distribution - BackBox
BackBox is a penetration test and security assessment oriented Ubuntu-based Linux distribution providing a network and informatic systems analysis toolkit. It includes a complete set of tools required for ethical hacking and security testing... -
Pentest Distro Linux - Weakerth4n
Weakerth4n is a penetration testing distribution which is built from Debian Squeeze.For the desktop environment it uses Fluxbox... -
The Amnesic Incognito Live System - Tails
Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and circumvent censorship... -

Penetration Testing Distribution - BlackArch
BlackArch is a penetration testing distribution based on Arch Linux that provides a large amount of cyber security tools. It is an open-source distro created specially for penetration testers and security researchers... -

The Best Penetration Testing Distribution - Kali Linux
Kali Linux is a Debian-based distribution for digital forensics and penetration testing, developed and maintained by Offensive Security. Mati Aharoni and Devon Kearns rewrote BackTrack... -

Friendly OS designed for Pentesting - ParrotOS
Parrot Security OS is a cloud friendly operating system designed for Pentesting, Computer Forensic, Reverse engineering, Hacking, Cloud pentesting...
Sunday, March 6, 2016
Hacking Ebooks ++ V
Best Hacking EBooks 2016 – In the Era of Teenagers many of want to Become a “Hacker” But In-fact It is not an Easy Task because Hacker’s have Multiple Programming Skills and Sharp Mind that Find Vulnerability in the Sites, Software and Other types of Application. If You want to become a Hacker you need to Spend most of the Time on your Computer to Learn New Technologies and Reading Hacking Book that can Help you to Become a Ethical Hacker. First You need to Read Hacking Books Carefully then Perform Practically not for Hacking Purpose Just only for Educational Purpose.
Hacking Ebooks ++ IV
Best Hacking EBooks 2016 – In the Era of Teenagers many of want to Become a “Hacker” But In-fact It is not an Easy Task because Hacker’s have Multiple Programming Skills and Sharp Mind that Find Vulnerability in the Sites, Software and Other types of Application. If You want to become a Hacker you need to Spend most of the Time on your Computer to Learn New Technologies and Reading Hacking Book that can Help you to Become a Ethical Hacker. First You need to Read Hacking Books Carefully then Perform Practically not for Hacking Purpose Just only for Educational Purpose.
Hacking Ebooks ++ III
Best Hacking EBooks 2016 – In the Era of Teenagers many of want to Become a “Hacker” But In-fact It is not an Easy Task because Hacker’s have Multiple Programming Skills and Sharp Mind that Find Vulnerability in the Sites, Software and Other types of Application. If You want to become a Hacker you need to Spend most of the Time on your Computer to Learn New Technologies and Reading Hacking Book that can Help you to Become a Ethical Hacker. First You need to Read Hacking Books Carefully then Perform Practically not for Hacking Purpose Just only for Educational Purpose.
Hacking Ebooks ++ II
Best Hacking EBooks 2016 – In the Era of Teenagers many of want to Become a “Hacker” But In-fact It is not an Easy Task because Hacker’s have Multiple Programming Skills and Sharp Mind that Find Vulnerability in the Sites, Software and Other types of Application. If You want to become a Hacker you need to Spend most of the Time on your Computer to Learn New Technologies and Reading Hacking Book that can Help you to Become a Ethical Hacker. First You need to Read Hacking Books Carefully then Perform Practically not for Hacking Purpose Just only for Educational Purpose.
Hacking Ebooks ++
Best Hacking EBooks 2016 – In the Era of Teenagers many of want to Become a “Hacker” But In-fact It is not an Easy Task because Hacker’s have Multiple Programming Skills and Sharp Mind that Find Vulnerability in the Sites, Software and Other types of Application. If You want to become a Hacker you need to Spend most of the Time on your Computer to Learn New Technologies and Reading Hacking Book that can Help you to Become a Ethical Hacker. First You need to Read Hacking Books Carefully then Perform Practically not for Hacking Purpose Just only for Educational Purpose.
Multipurpose Sniffer - Ettercap
Ettercap is a free and open source network security tool for man-in-the-middle attacks on LAN. It can be used for computer network protocol analysis and security auditing. It runs on various Unix-like operating systems including Linux, Mac OS X, BSD and Solaris, and on Microsoft Windows. It is capable of intercepting traffic on a network segment, capturing passwords, and conducting active eavesdropping against a number of common protocols.
Functionality
Ettercap works by putting the network interface into promiscuous mode and by ARP poisoning the target machines. Thereby it can act as a ‘man in the middle’ and unleash various attacks on the victims. Ettercap has plugin support so that the features can be extended by adding new plugins.
Features
Ettercap supports active and passive dissection of many protocols (including ciphered ones) and provides many features for network and host analysis. Ettercap offers four modes of operation:
ºIP-based: packets are filtered based on IP source and destination.
ºMAC-based: packets are filtered based on MAC address, useful for sniffing connections through a gateway.
ºARP-based: uses ARP poisoning to sniff on a switched LAN between two hosts (full-duplex).
ºPublicARP-based: uses ARP poisoning to sniff on a switched LAN from a victim host to all other hosts (half-duplex).
In addition, the software also offers the following features:
Character injection into an established connection: characters can be injected into a server (emulating commands) or to a client (emulating replies) while maintaining a live connection.
SSH1 support: the sniffing of a username and password, and even the data of an SSH1 connection. Ettercap is the first software capable of sniffing an SSH connection in full duplex.
HTTPS support: the sniffing of HTTP SSL secured data—even when the connection is made through a proxy.
Remote traffic through a GRE tunnel: the sniffing of remote traffic through a GRE tunnel from a remote Cisco router, and perform a man-in-the-middle attack on it.
Plug-in support: creation of custom plugins using Ettercap’s API.
Password collectors for: TELNET, FTP, POP, IMAP, rlogin, SSH1, ICQ, SMB, MySQL, HTTP, NNTP, X11, Napster, IRC, RIP, BGP, SOCKS 5, IMAP 4, VNC, LDAP, NFS, SNMP, Half-Life, Quake 3, MSN, YMSG
Packet filtering/dropping: setting up a filter that searches for a particular string (or hexadecimal sequence) in the TCP or UDP payload and replaces it with a custom string/sequence of choice, or drops the entire packet.
OS fingerprinting: determine the OS of the victim host and its network adapter.
Kill a connection: killing connections of choice from the connections-list.
Passive scanning of the LAN: retrieval of information about hosts on the LAN, their open ports, the version numbers of available services, the type of the host (gateway, router or simple PC) and estimated distances in number of hops.
Hijacking of DNS requests.
Dependencies:
ºLibpcap & dev libraries
ºLibnet1 & dev libraries
ºLibpthread & dev libraries
ºZlibc
ºLibtool
ºCMake 2.6
ºFlex
ºBison
ºSSL Dissection Required Dependencies
ºLibSSL & dev libraries
ºGTK Related Dependencies
ºLibGTK & dev libraries
ºNCurses Related Dependencies
ºLibncurses & dev libraries
ºFilter Related Regex Dependencies
ºLibpcre & dev libraries
Saturday, March 5, 2016
Lightweight MITM Proxy - HoneyProxy
HoneyProxy is a lightweight man-in-the-middle proxy that helps you analyze HTTP(S) traffic flows. It is tailored to the needs of security researchers and allows both real-time and log analysis. Being compatible with mitmproxy, it focuses on features that are useful in a forensic context and allows extended visualization capabilites.
HoneyProxy is developed as a HTML5 browser-based application working on top of a logging core written in Python. It is primarily developed by Maximilian Hils and mentored by Guillaume Arcas as part of the Honeynet Google Summer of Code 2012 project.
Features
ºAnalyze HTTP(S) traffic on the fly
ºFilter and highlight traffic, regex support included.
ºReport Generation for saved flows, including a live JS editor.
ºSave HTTP conversations for later analysis
ºMake scripted changes with Python, e.g. remove Cache Header.
ºbased on and compatible to mitmproxy.
ºcross-platform (Windows, OSX and Linux)
ºSSL interception certs generated on the fly
Lightweight MITM Proxy: HoneyProxy
Quick start
Download the latest release, a development snapshot or clone the git repo:
git clone --recursive git://github.com/mhils/HoneyProxy.git.
Install all dependencies:
pip install pyOpenSSL pyasn1 Twisted Autobahn
Windows users: Install the binaries for pyOpenSSL and Twisted manually.
Ubuntu / Debian users: Install twisted as a package (sudo apt-get install python-twisted)
Start HoneyProxy with:
python honeyproxy.py
or
python honeyproxy.py --help.
If you don’t use a modern browser, a kitten will die. We currently support both Firefox and Chrome!
Most command line parameters are documented in the mitmproxy docs.
Dependencies
ºPython 2.7.x.
ºpyOpenSSL 0.12 or newer.
ºpyasn1 0.1.2 or newer.
ºTwisted 12.3.0 or newer.
Search
A major feature of HoneyProxy is the ability to filter requests based on different criteria. HoneyProxy has a rich set of modifiers to allow fine-grained search requests:
ºRegular Search: If you don’t supply any modifiers, HoneyProxy will show all flows that contain the given string. This is case-insensitive.
ºCase Sensitive Search: If your search request starts with an equal sign ( =filter ), search is performed case-sensitive.
ºInverse Search: If your search request starts with an exclamation mark ( !filter ), all requests that don’t match the criteria are displayed.
ºRegular Expressions: If your search request starts with a tidle sign ( ~param=(foo|bar|[\d]+) ), your input is treated as a regular expression. You can combine this with the inverse modifier (!~). Please note that regular expressions are always case-sensitive
Dump conversations into a directory structure
HoneyProxy can dump all response contents into a directory-like structure. For example if you request example.com/files/foo.zip, foo.zip will be placed in $dumpdir/example.com/files/foo.zip. However, there are some restrictions with the filesystem:
ºAs file and folder names are limited to different lengths on different operating systems, HoneyProxy is going to cut off long directory and/or file names ([...] in the folder name or file name is a good indicator for this).
ºThe content of a unique URL is not guaranteed to be identical when calling it twice. To handle this transparently, HoneyProxy creates a second file if the response contents don’t match.
ºAs example.com/foo/ can be both a resource and a directory, HoneyProxy appends [dir] to a directory if a resource with the same name exists. This might lead to the problem that example.com/foo/bar.zip and example.com/foo[dir]/baz.zip seem to be in the same directory.
Conclusion: Don’t assume that the --dump-dir option creates an exact representation of your HTTP requests. If you keep that in mind, it’s still a very powerful tool for visualization!
Multiuser Capability
Due to its client-server architecture, HoneyProxy is not restricted to a single GUI Session. You can open the HoneyProxy GUI on multiple machines and browse the same dump simultaneously. It also works in live mode, all client’s get a notice of new flows.
Usage Instructions
When connection from a remote machine, make sure to open both the GUI and the WebSocket port (8081 and 8082 by default). Feel free to configure them using the corresponding command line flags.
The HoneyProxy GUI is protected from unauthorized access via Basic Auth. To access the GUI, you need valid credentials (HoneyProxy adds them by default when opening the browser). While the username is constant, the password is usually a 32 digit random string. It is displayed on the command line after HoneyProxy has been started. If you are working in a trusted environment, you can change this by using the --api-auth command line flag.
Basic Auth User: honey
Basic Auth Pass: displayed on the command line or specified by --api-auth
Programmatic Access with JavaScript / API
While HoneyProxy has inherited a great Python API from mitmproxy (docs), it also provides access to flows via JavaScript. This can be extremly powerful for developers who are interested in extending HoneyProxy or JavaScript hackers who want to run custom queries on a set of flows. For short, HoneyProxy stores all flows in a Backbone Collection (window.HoneyProxy.traffic). A flow contains a request object, a response object, an error object and its unique id. For easified access, we have ES5 proxy objects for both request and response directly as attributes of the Flow (e.g. HoneyProxy.traffic.get(0).request.host). They are stateless wrappers with ES5 getters for the original model attributes.
HoneyProxy mitmproxy
HoneyProxy is build on top of the excellent mitmproxy. It provides us with a solid proxy base and a great API. The features below are inherited by HoneyProxy and are part of the mitmproxy code base. We show them here, because they are highly useful and also part of HoneyProxy. Credit goes to mitmproxy though
Anticache
If you want to access request content of a cached file, specify the --anticache command line flag. It removes all caching headers from HTTP requests. This is a feature of mitmproxy and documented in the mitmproxy docs.
Transparent Mode
This is an currently undocumented feature of the latest mitmproxy trunk code, but it’s already in HoneyProxy! Just run HoneyProxy with the -T switch and add a proper iptables rule. This currently only works on Linux.
Replacements
This is a feature of mitmproxy and documented in the mitmproxy docs.
Setting up SSL interception
This is a feature of mitmproxy and documented in the mitmproxy docs. The default certificate directory for HoneyProxy is ~/mitmproxy/.
Programmatic Access with Python – mitmproxy Scripts
HoneyProxy has inherited a great Python API from mitmproxy (docs). You can find a lot of examples in the mitmproxy repo.
So much more…
If you find a command-line switch that is not documented here, head over to the mitmproxy website for details
Browser Based Security Framework - Mantra Janus
7:26:00 PM
Hackers Tools, Information Gathering, Pentest Tools, SQLinjection, Web Applications
No comments
OWASP Mantra is a collection of free and open source tools integrated into a web browser, which can become handy for students, penetration testers, web application developers,security professionals etc. It is portable, ready-to-run, compact and follows the true spirit of free and open source software.
Browser Based Security Framework: Mantra Janus
OWASP Mantra is a free and open source security toolkit with a collection of add-ons and scripts based on Firefox and Chromium. It is intended for web application penetration testers, web application developers, security professionals, etc. Earlier versions of Mantra used Firefox as base named “Mantra Security Toolkit’. From September 2011 onwards Mantra started offering a new distribution called ‘MoC’, based on Google Chrome. As of May 2012, both the products are available and are active.
Features
Mantra comes packed with many tools and other extensions that are useful for web application penetration testing. Some additional changes are applied to the normal Firefox to avoid extra traffic and noises.
Other notable features include:
ºFireCAT/ KromCAT menu structure makes the tools menu more organised and easy to access.
ºSidebar of Mantra provides quick access to tools and other features
ºThe awesome bar acts as URL bar and search bar at the same time. Various details about the currently visited webpage are also shown in the awesome bar.
ºAdd to search bar feature helps users to customise default search feature of awesome bar.
ºURL increment/ decrement buttons helps in applying quick changes to the URL.
ºHackery aka The Open Pentest Bokkmarks Collection gives links to various resources and portal that are related to penetration testing.
ºGalley bookmarks provides links to various on-line penetration testing related services.
ºProxy, Cookie and Cache management tools
ºFTP, SSH, REST and SQLite clients
Tools
The OWASP Mantra Security Toolkit has tools under the following categories:
ºInformation gathering
ºEditors
ºNetwork utilities
ºMiscellaneous
ºApplication auditing
ºProxy
Mantra is lite, flexible, portable and user friendly with a nice graphical user interface. You can carry it in memory cards, flash drives, CD/DVDs, etc. It can be run natively on Linux, Windows and Mac platforms. It can also be installed on to your system within minutes. Mantra is absolutely free of cost and takes no time for you to set up.
Passive-Analysis Tool - Watcher
Watcher is a runtime passive-analysis tool for HTTP-based Web applications. Being passive means it won’t damage production systems, it’s completely safe to use in Cloud computing, shared hosting, and dedicated hosting environments. Watcher detects Web-application security issues as well as operational configuration issues. Watcher provides pen-testers hot-spot detection for vulnerabilities, developers quick sanity checks, and auditors PCI compliance auditing. It looks for issues related to mashups, user-controlled payloads (potential XSS), cookies, comments, HTTP headers, SSL, Flash, Silverlight, referrer leaks, information disclosure, Unicode, and more.
Watcher is built as a plugin for the Fiddler HTTP debugging proxy available at www.fiddlertool.com. Fiddler provides all of the rich functionality of a good Web/HTTP proxy. With Fiddler you can capture all HTTP traffic, intercept and modify, replay requests, and much much more. Fiddler provides the HTTP proxy framework for Watcher to work in, allowing for seamless integration with today’s complex Web 2.0 or Rich Internet Applications. Watcher runs silently in the background while you drive your browser and interact with the Web-application.
A Passive tool for Web Security Testing and Auditing
Watcher is a runtime passive-analysis tool for HTTP-based Web applications. Being passive means it won’t damage production systems, it’s completely safe to use in Cloud computing, shared hosting, and dedicated hosting environments. Watcher detects Web-application security issues as well as operational configuration issues. Watcher provides pen-testers hot-spot detection for vulnerabilities, developers quick sanity checks, and auditors PCI compliance auditing. It looks for issues related to mashups, user-controlled payloads (potential XSS), cookies, comments, HTTP headers, SSL, Flash, Silverlight, referrer leaks, information disclosure, Unicode, and more.
Major Features:
1. Passive detection of security, privacy, and PCI compliance issues in HTTP, HTML, Javascript, CSS, and development frameworks (e.g. ASP.NET, JavaServer)
2. Works seamlessly with complex Web 2.0 applications while you drive the Web browser
3. Non-intrusive, will not raise alarms or damage production sites
4. Real-time analysis and reporting – findings are reported as they’re found, exportable to XML, HTML, and Team Foundation Server (TFS)
5. Configurable domains with wildcard support
6. Extensible framework for adding new checks
Watcher is built as a plugin for the Fiddler HTTP debugging proxy available at www.fiddlertool.com. Fiddler provides all of the rich functionality of a good Web/HTTP proxy. With Fiddler you can capture all HTTP traffic, intercept and modify, replay requests, and much much more. Fiddler provides the HTTP proxy framework for Watcher to work in, allowing for seamless integration with today’s complex Web 2.0 or Rich Internet Applications. Watcher runs silently in the background while you drive your browser and interact with the Web-application.
Watcher is built in C# as a small framework with 30+ checks already included. It’s built so that new checks can be easily created to perform custom audits specific to your organizational policies, or to perform more general-purpose security assessments. Examples of the types of issues Watcher will currently identify:
ºASP.NET VIEWSTATE insecure configurations
ºJavaServer MyFaces ViewState without cryptographic protections
ºCross-domain stylesheet and javascript references
ºUser-controllable cross-domain references
ºUser-controllable attribute values such as href, form action, etc.
ºUser-controllable javascript events (e.g. onclick)
ºCross-domain form POSTs
ºInsecure cookies which don’t set the HTTPOnly or secure flags
ºOpen redirects which can be abused by spammers and phishers
ºInsecure Flash object parameters useful for cross-site scripting
ºInsecure Flash crossdomain.xml
ºInsecure Silverlight clientaccesspolicy.xml
ºCharset declarations which could introduce vulnerability (non-UTF-8)
ºUser-controllable charset declarations
ºDangerous context-switching between HTTP and HTTPS
ºInsufficient use of cache-control headers when private data is concerned (e.g. no-store)
ºPotential HTTP referer leaks of sensitive user-information
ºPotential information leaks in URL parameters
ºSource code comments worth a closer look
ºInsecure authentication protocols like Digest and Basic
ºSSL certificate validation errors
ºSSL insecure protocol issues (allowing SSL v2)
ºUnicode issues with invalid byte streams
ºSharepoint insecurity checks
ºmore….
Reducing false positives is a high priority, suggestions are welcome. Right now each check takes steps to reduce false positives, some better than others, and checks can be individually disabled if they’re generating too much noise.
Platform Independent Network Packet Generator - Hyenae
Hyenae is a highly flexible platform independent network packet generator. It allows you to reproduce several MITM, DoS and DDoS attack scenarios, comes with a clusterable remote daemon and an interactive attack assistant.
Platform Independent Network Packet Generator
Features
ºARP-Request flooding
ºARP-Cache poisoning
ºPPPoE session initiation flooding
ºBlind PPPoE session termination
ºICMP-Echo flooding
ºICMP-Smurf attack
ºICMP based TCP-Connection reset
ºTCP-SYN flooding
ºTCP-Land attack
ºBlind TCP-Connection reset
ºUDP flooding
ºDNS-Query flooding
ºDHCP-Discover flooding
ºDHCP starvation attack
ºDHCP-Release forcing
ºCisco HSRP active router hijacking
ºPattern based packet address configuration
ºIntelligent address and address protocol detection
ºSmart wildcard-based randomization
ºDaemon for setting up remote attack networks
ºHyenaeFE QT-Frontend support
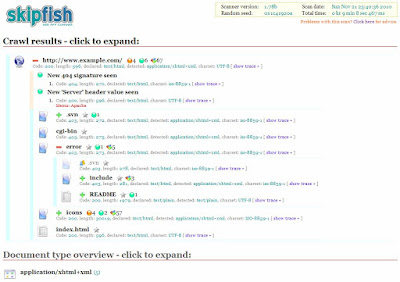
Web Application Security Reconnaissance - Skipfish
Skipfish is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.
Key features:
High speed:
pure C code, highly optimized HTTP handling, minimal CPU footprint – easily achieving 2000 requests per second with responsive targets.
Ease of use:
heuristics to support a variety of quirky web frameworks and mixed-technology sites, with automatic learning capabilities, on-the-fly wordlist creation, and form autocompletion.
Cutting-edge security logic:
high quality, low false positive, differential security checks, capable of spotting a range of subtle flaws, including blind injection vectors.
The tool is believed to support Linux, FreeBSD, MacOS X, and Windows (Cygwin) environments.
SQL Injection framework - Seringa
Seringa – SQL Injection framework
Seringa (Romanian for seringe) is an SQL injection framework featuring high customizability and a user-friendly interface. It is completely open source. Uses the .NET 4.0 framework and Windows Presentation Foundation(WPF) for the GUI. With regard to design it utilizes the Strategy Pattern to distinguish between various SQLi strategies whilst storing other relevant data such as exploits, payloads and patterns in xml files so that the framework can be easily customized from the outside(a manifestation of the Open-Closed Principle).
Seringa allows you to:
ºscan Google search results given a search string
ºtest search results for SQLi vulnerability
ºtest a single url for vulnerability
ºextract a database structure(databases,tables,columns) in a tree form
ºexecute given payloads and receive results(some predefined queries include current database name, current database user, current database version etc)
ºsave your penetration testing process to a file(mapping file) and load it later
ºuse a proxy(regular or socks) when testing
Concepts: Injection Strategies
ºways of actually running a SQL injection
ºrequire their own distinct classes in the code
ºnot modifiable without recompiling
ºthe 2 available types at the time of writing are “UNION Based”(referring to the use of the UNION SQL command) and “ERROR Based”(referring to errors being spilled out by the web application)
ºInjection Strategy classes are required to implement the IInjectionStrategy interface DBMSs
ºshort for Database Management System
ºrefer to the underlying DBMS that the web application sends commands to
ºthe DBMS values seen in the GUI are extracted from the exploits file(see the Exploits concept) Exploits
ºthe actual SQL commands that cause a vulnerable system to do what the penetration tester wants
ºthey are configurable in the exploits.xml file that is found in the xml folder each node in sed file represents a single exploit
ºeach exploit works for a particular DBMS as specified by the dbms attribute of the node Payloads
ºwhat the penetration tester wants to do to the system
ºconfigurable in the payloads.xml file
ºalso dependable on the DBMS Patterns
ºused when testing if a particular url is SQL injectable
ºeach pattern is a message that the targeted web application might output when it’s tested if it is vulnerable to SQLi attacks
ºconfigurable in patterns.xml Ipcheckers
ºwhen using a proxy with Seringa you might want to check what your ip actually is from within the application
ºthis can easily be done using a free ip checker site
ºthe ipcheckers.xml file allows for the free site to be configured to your favourite ip checker site
Search
Translate
Popular Posts
-
Introduction This tool is made to automate the process of retrieving secrets in the public APIs on [swaggerHub](https://app.swaggerhub.com...
-
Remote adminitration tool for android Features Notifications listener SMS listener Phone call recording Image capturing and sc...
-
AzSubEnum is a specialized subdomain enumeration tool tailored for Azure services. This tool is designed to meticulously search and identify...
Categories
#Snowden
Active Directory Attacks
Analysis
Android
Android Hack
Android Pentest
Anonimato
Anonymity
Anti-Forensic
Anti-Forensic Tools
Anti-Government
Anti-System
Apache
API Hacking
APK
ARM
Assembly
Attack Map
Auditing Tool
Automation Tools
AvKill
AWS Pentest
Backdoor
Bind
BlueTeam
Bluetooth
Bot
botnet/DDoS
Bounty
Brute Force
Bypass
Certificate
Cheat Sheet
Cloud Forensics
Cloud Pentest
Courses
Cryptography
CTF Engine
CVEs
Cyber Forensics
Cyber War
Data Base
DeepWeb
DevSecOps
Disassembler
DLL Hijacking
Dns Enumeration
Dns Recon
Dns Spoof
Documentary
DoS
Downloads
DUMP
Elearn Security
Email Hacking
Encrypted DNS
Engenharia Reversa
Enumeration
Evasion
EXIF
Exploit
Exploitation Tools
Exposed Leaked
Fake
Filmes e Documentários
Fingerprint
Firewall
Footprint
Frameworks
Fuck The System
Fuzzer
GeoIP
Google Hacking
Hackers
Hackers News
Hackers Tools
Hacking
Hacking Ebook's
Hacking Vídeos
Hacktivism
Hardening
Hardware
Hardware Hack
Hidden
HIDS
Honeypots
How to exit the Matrix
IDS
IDS/IPS
Incident Response
Information Gathering
iOS
IoT
JAVA
Kali
Kali Linux
Keylogger
Labs
Leaked
Leaks
Leave The Matrix
Linux
Linux System
Mac
Malware
Malware Analysis
MetaSploit
Mind Map
MIPS
MITM
Monitoring
Movies
Network
Networking
New World Order
Nmap
Offensive Politics
Offensive Sec
OffSec
OffSec Exclusive Tools
Open Your Mind
OpenSSL
Os Sec
OSINT Tools
OWASP ZAP Scanner
Password Capture
Password Cracking
Passwords
Payload
PCC
PDF
Pentest
Pentest Tools
Phishing Attacks
Phones
PHP
Port Scan
Post-Exploitation Tool
PowerShell
Pr1v8
Privacidade
Privacy
Privilege Escalation
Projects
Proxy
Python
Ransomware
RAT
Recover File and Disk Analyzer
Red Team
Redes
Remote
Reverse
Reverse Engineering
Reverse Shell
RFID
Rootkit
Scan Tools
Security
Security Ebook's
Seriados
Series
Shell
Shell PHP
Shellcode
Shodan
Sniffer
Social Engineering
Source Code
Spoofing
SQLinjection
SSL
Stealer
Steganography
Stress Testing
Study
Subdomain Discovery
SysInternals
Telnet
The Theory of Conspiracy
Threat Intelligence
Tools
Tor
Trojan
Tutorials
Unix System
URL Inspector
Usb Boot
Virtual Machine
Virus
VoIP
VPN
Vulnerabilities
Vulnerability Analysis
WAF
Web Applications
Web Pentesting
Whois
Wifi-Hacks
Windows
Wireless Hacking
Word List
WordPress
X86
XSS
 0Day to Buy
0Day to Buy