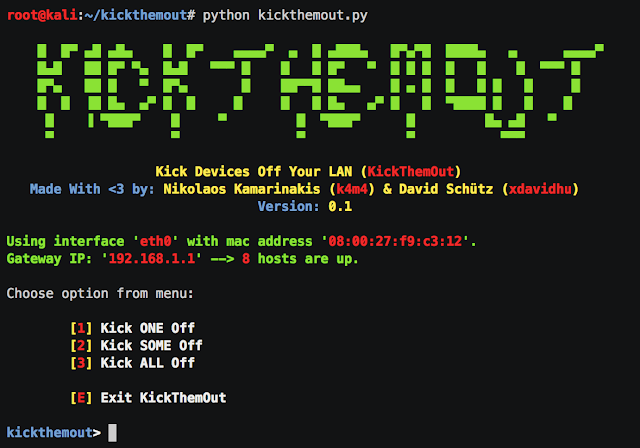
A tool to kick devices out of your network and enjoy all the bandwidth for yourself. It allows you to select specific or all devices and ARP spoofs them off your local area network.
Compatible with Python 2.6 & 2.7.
Authors: Nikolaos Kamarinakis & David Schütz
Installation
You can download KickThemOut by cloning the Git Repo and simply installing its requirements:
$ git clone https://github.com/k4m4/kickthemout.git
$ cd kickthemout
$ pip install -r requirements.txtDemo
Here's a short demo:

(For more demos click here )
Disclaimer
KickThemOut is provided as is under the MIT Licence (as stated below). It is built for educational purposes only. If you choose to use it otherwise, the developers will not be held responsible. In brief, do not use it with evil intent.
 0Day to Buy
0Day to Buy